Web Application Security Risks
Identifying the Threats We Face:
We will begin by looking at the specific security threats facing a modern web application. The first step in building a secure application is to understand the nature of the risks, so that we can think about how to protect against those risks.
Access to Sensitive Data:-
Part of our job as web application designers and programmers is to ensure that any data the user entrusts to us are safe, as are any data that we are given from other departments. When we expose part of this information to users of our web application, it must be in such a way that they see only the information for other users.
All of these are terrible scenarios, but the two most commonly seen that cause huge problems are leakage of username & passwords and another one is credit card numbers.
Passwords may be less obviously interesting. Once an attacker has obtained access to sensitive data inside your application, you may be asking why passwords would have any further use. The answer is that users commonly re-use passwords on different websites. The username and password sagar raj used to sign up for your photo sharing app stand a good chance of being the same username and password that he uses for his online banking.
The value of credit card number is obvious-- anyone obtaining a list of valid numbers along with expiration dates, cardholder names, and so on, can either use the data themselvers, or more commonly, sell a list of card numbers to the highest bidder.
Reducing the Risk:-
To reduce the risk of exposure, you need to limit the methods by which information can be accessed and limit the people who can access it. This process involves designing with security in mind, configuring your server and software properly, programming carefully, testing thoroughly, removing unnecessary services from the web server, and requiring authentication.
You need to design, configure, code, and test carefully to reduce the risk of a successful attack and, equally important, to reduce the chance that an error will leave your information open o accidental exposure.
Attack that involve accessing or modifying your data as it travels over the network are known as man-in-the-middle (MITM) attacks.
To protects confidential information, you can encrypt it before it is sen across a network and decrypt it at the other end. Web servers often use Secure Sockets Layer (SSL) to accomplish this as data travels between web servers and browsers. This is a fairly low-cost, low-effort way of securing transmissions, but because your server needs to encrypt and decrypt data rather than simply send and receive it, the number of visitors per second that a machine can serve is reduced.
Denial of Service Attack (DOS Attack):
One of the most difficult threats to guard against is denial of service. Denial of service (DoS) occurs when somebody's actions make it difficult or impossible for users to access a service, or delay their access to a time-critical service.
As with some of the other threats, a DoS can come from forces other than malicious attack. A misconfigured network or an influx of users (after, say, your application being featured on a popular tech blog) can have the same effect.
In early 2013, a series of distributed denial of service (DDoS) attacks were made against US financial institutions such as American Express and Well Fargo. These sites are accustomed to high levels of traffic, and have excellent security teams working on them, but they are still vulnerable to being shut down for hours by a DoS attack.
Famous DDoS Attacks | The Largest DDoS Attacks Of All Time
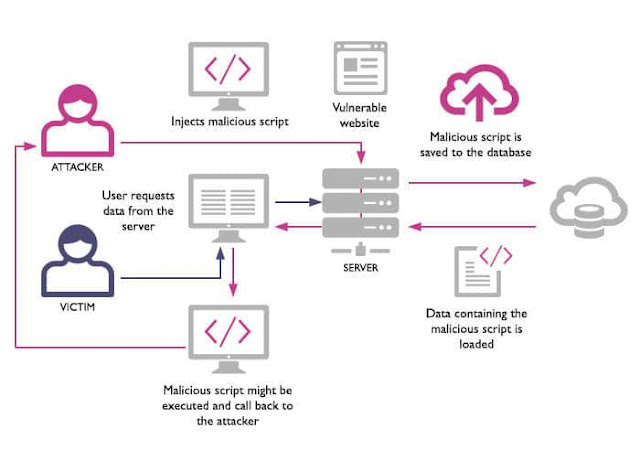
Malicious Code Injection:
One type of attack that has been particularly effective over the years via the web is what is called code injection. The well known of these is Cross Site Scripting (known as XSS, so as not to be confused with Cascading style sheets-CSS). What is particularly troubling about these attacks is that no obvious or immediate loss of data occurs, but instead some soft of code executes, causing varying degrees of information loss or redirection of users, possibly without their even noticing it.
It's also possible to take advantage of vulnerabilities in your code, your installed applications, or your configuration to upload arbitrary code to run on your web server, leading to a compromised web server.
Building a Secure Web Application
Monitoring Security
After we finish developing our web applications and deploy it to production servers for people to begin using, our job is not complete. Part of security is monitoring the system as it operates, looking at logs and other files to see how the system is performing and being used. Only by keeping a close eye on the operation of the system (or by writing and running tools to do portions of this for us), can we see whether ongoing security problems exist and find areas where we might need to spend some time developing more secure solutions.
Security is, unfortunately, an going battle and, in a certain hyperbolic sense, a battle that can never be won. Constant vigilance, improvements to our system, and rapid reaction to any problems are the price to be paid for a smoothly operating web application.
Securing Your Code
Making a good effort at securing your code requires you to think at a granular level, including inspecting each of the components individually and looking at how to improve their security, we begin in this section by investigating the things we can do to help keep our code safe.
Filtering User Input
One of the most important things we can do in our web applications to make them more secure is to filter all user input.
Application developers must filter all input that comes from external sources. This does not mean that we should design a system with the assumption that all our users are crooks. We still want them to feel welcome and indeed encourage them to use our web application. We just want to be sure that we are prepared at any point for of our system.
If we do this filtering effectively, we can reduce the number of external threats substantially and massively improve the robustness of our system. Even if we are pretty sure that we trust the users, we cannot be certain that they do not have some thype of spyware program or other such thing that is modifying or sending new requests to our server. So really, never trust the users.
Keep Software Up-to-Date
One of the easiest ways to help the security of your system is to ensure that your are always running the latest and most secure version of the software you are using.
Prepare for Dos and DDoS Attack:
One of the more frightening attacks seen today is the denial of service (DoS) attack.
Web application security risks, network dos attacks and the even more alarming distributed denial of service (DDoS) attacks use hijacked computers, worms, or othe devices to exploit weaknesses in software installations, or even those inherent within the design of protocols such as TCP/IP themselves to swamp a computer and prevent it from replying to any connection request from legitimate clients.
Unfortunately, this type of attack is very difficult to prevent and respond to. Some network appliance vendors sell equipment to help mitigate the risks and effects of DoS attacks, but there are no comprehensive solutions against them yet.
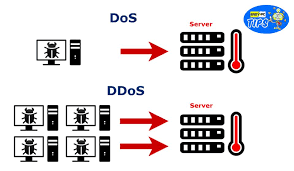
The Difference Between DoS and DDos Attacks
The DoS attack typically uses one computer and one Internet connection to flood a targeted system or resource. The DDoS attack uses multiple computers and Internet connections to flood the targeted resource.Physically Secure the Server
We mentioned previously that one of our security threats is somebody coming into our building, unplugging the server computer, and simply walking off with it. This is, tragically, not a joke. With the average server not being a terribly cheap piece of hardware, the motivations for stealing server computers are not limited to corporate espionage and intellectual theft. Some people might just want to steal the computer for resale.
Thus, it is critical that servers used to run your web applications are kept in a secure environment, with only authorized people given access to it and specific process in place for granting and revoking access to different people.
I Hope you like this article Thanks for read this article.
Please share this article to your friends and family members..
subscribe to our blog for more articles...









1 Comments
TeachTech
ReplyDeleteTeachTech
TeachTech
TeachTech
TeachTech
TeachTech
TeachTech
TeachTech
TeachTech
TeachTech
For More Information Please Comment