Advance Network security
- Now-a-days the internet usage is in great swing in online banking and e-commerce, in which case the security of the network becomes more important.
- Securing your network from attacks and unauthorized access is an important part of any architecture.
- The use of computers has been growing rapidly, from sending confidential communications to e-business. On the one hand, while it has increased a lot of facilities, on the other hand, due to security related problems, there are also two-four. Keeping the network secure has become a major challenge, so that messages passing through network traffic can safely reach their destination.
Goals of Network Security:
Network security is not only concerned about the security of the computers at each end of
the communication chain; however, it aims to ensure that the entire network is secure.
Network security entails protecting the usability, reliability, integrity, and safety of network
and data. Effective network security defeats a variety of threats from entering or spreading
on a network.
The primary goal of network security are Confidentiality, Integrity, and Availability. These
three pillars of Network Security are often represented as CIA triangle.
 |
| Sagar IT World is not the owner of this picture .Owner of this picture is https://thecoderzone.com/security-goals/ |
- Confidentiality. The function of confidentiality is to protect precious business data from unauthorized persons. Confidentiality part of network security makes sure that the data is available only to the intended and authorized persons.
- Integrity. This goal means maintaining and assuring the accuracy and consistency of data. The function of integrity is to make sure that the data is reliable and is not changed by unauthorized persons.
- Availability. The function of availability in Network Security is to make sure that the data, network resources/services are continuously available to the legitimate users, whenever they require it
Network Security:
Network security is protecting the communication of resources within and outside of your network. The goal is to limit exposure at the network layer across your services and systems. By limiting this exposure, you decrease the likelihood that your resources can be attacked. In the focus on network security, efforts can be focused on the following areas:
Securing traffic flow between applications and the internet focuses on limiting exposure outside your network. Network attacks will most frequently start outside your network, so by limiting the internet exposure and securing the perimeter, the risk of being attacked can be reduced.
Securing traffic flow among applications focuses on data between applications and their tiers, between different environments, and in other services within your network. By limiting exposure between these resources, you reduce the effect a compromised resource can have. This can help reduce further propagation within a network.
Securing traffic flow between users and the application focuses on securing the network flow for your end users. This limits the exposure your resources have to outside attacks, and provides a secure mechanism for users to utilize your resources.
If we start on the perimeter of the network, we're focused on limiting and eliminating attacks from the internet. A great first place to start is to assess the resources that are internet-facing, and only allow inbound and outbound communication where necessary. Identify all resources that are allowing inbound network traffic of any type, and ensure they are necessary and restricted to only the ports/protocols required. Azure Security Center is a great place to look for this information, as it will identify internet-facing resources that don't have network security groups (NSG) associated with them, as well as resources that are not secured behind a firewall.- Securing traffic flow between applications and the internet
- Securing traffic flow among applications
- Securing traffic flow between users and the application
Securing traffic flow between applications and the internet focuses on limiting exposure outside your network. Network attacks will most frequently start outside your network, so by limiting the internet exposure and securing the perimeter, the risk of being attacked can be reduced.
Securing traffic flow among applications focuses on data between applications and their tiers, between different environments, and in other services within your network. By limiting exposure between these resources, you reduce the effect a compromised resource can have. This can help reduce further propagation within a network.
Securing traffic flow between users and the application focuses on securing the network flow for your end users. This limits the exposure your resources have to outside attacks, and provides a secure mechanism for users to utilize your resources.
Internet Protection:
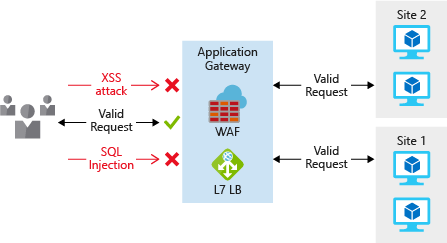
To provide inbound protection at the perimeter, there are a couple of ways to do this. Application Gateway is a Layer 7 load balancer that also includes a web application firewall (WAF) to provide advanced security for your HTTP-based services. The WAF is based on rules from the OWASP 3.0 or 2.2.9 core rule sets, and provides protection from commonly-known vulnerabilities such as cross-site scripting and SQL injection.
For protection of non-HTTP-based services or for increased customization, network virtual appliances (NVA) can be used to secure your network resources. NVAs are similar to firewall appliances you might find in on-premises networks, and are available from many of the most popular network security vendors. NVAs can provide greater customization of security for those applications that require it, but can come with increased complexity, so careful consideration of requirements is advised.
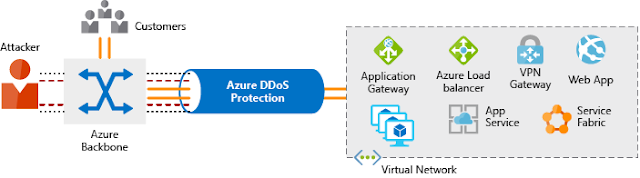
Any resource exposed to the internet is at risk of being attacked by a denial-of-service attack. These types of attacks attempt to overwhelm a network resource by sending so many requests that the resource becomes slow or unresponsive. To mitigate these attacks, Azure DDoS provides basic protection across all Azure services and enhanced protection for further customization for your resources. DDoS protection blocks attack traffic and forwards the remaining traffic to its intended destination. Within a few minutes of attack detection, you are notified using Azure Monitor metrics.
An illustration showing Azure DDoS protection installed between virtual network and external user requests. The Azure DDoS protection blocks malicious traffic attack but forwards the legitimate traffic to the intended destination.
I Hope you like this article Thanks for read this article.
Please share this article to your friends and family members..
subscribe to our blog for more articles...








0 Comments
For More Information Please Comment